티스토리 뷰
Hello, My friends who visit to my blog.
How have you been these days? In my case, I have been working OpenStack project nowadays. so I am very busy and tired now. Actually, I wanted to post in English on my blog continue. but I have to had solving the virous problems everyday and everytime. so I didn't have any time for posting in English on my blog.
Today, I will share about how to design OpenStack for security before I forget that I get my OpenStack experiance.
I visited openstack.org site for checking OpenStack deployment methods. and I discoverd OpenStack architecture is changed. Now OpenStack is not using only virtual machines. We can use various resources like bare metal, virtual machines and containers.
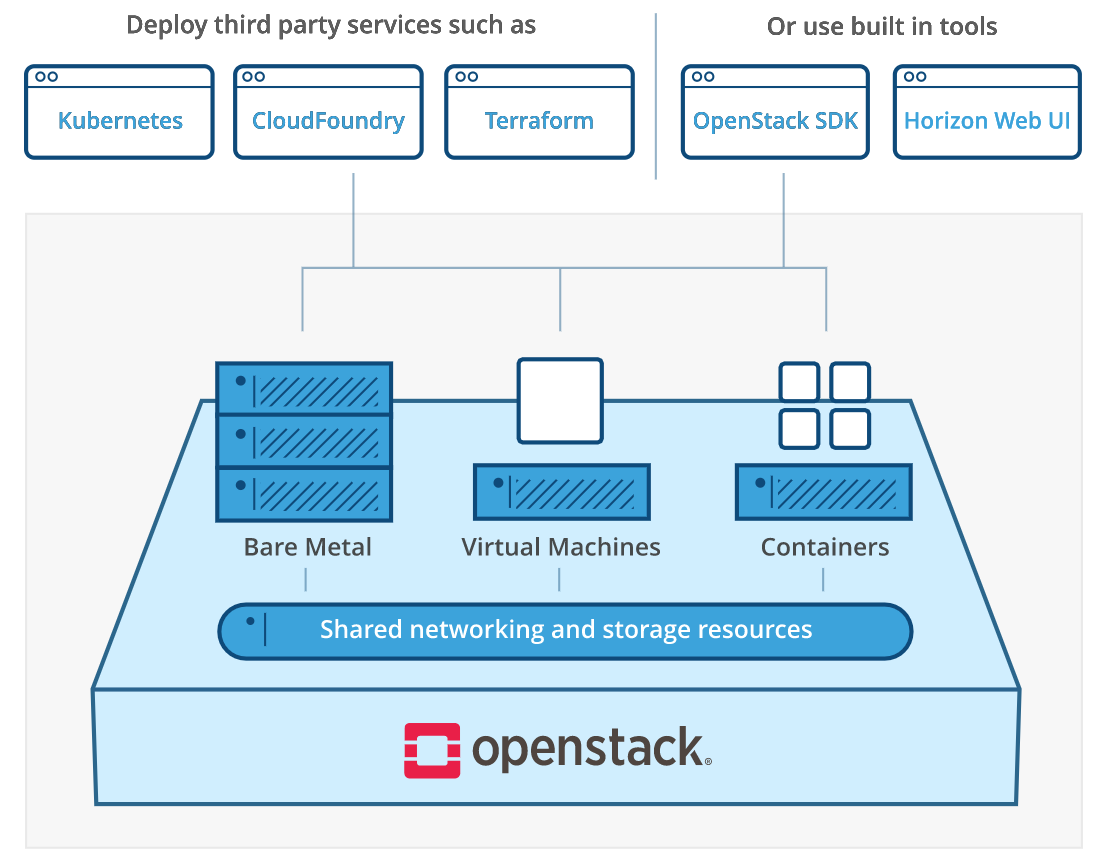
So how can we use our cloud resources more security? Openstack use REST API for using cloud resources. So it have http or https uri. Https is hypertext transfer protocol over secure. So https encrypted session data through ssl or tls protocol. ssl is secure socket layer. It needs certificate and secure key like below diagram.
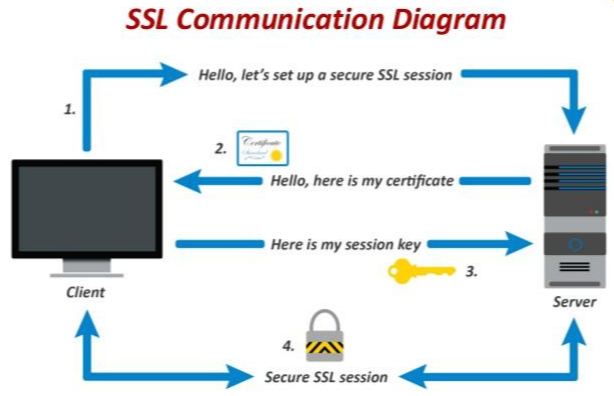
Most OpenStack environment configured in data center. so it need many servers and there are many servers. Therefore we need to manage a lot of server's secure key and certification. How can we manage these keys and certifications?
Red Hat Openstack 13 can install ssl/tls using IDM server. IDM Server provides to manage users, domains, certificates and servers. For using ssl/tls with IDM Server, it needs domain of all Openstack networks like below architecture.
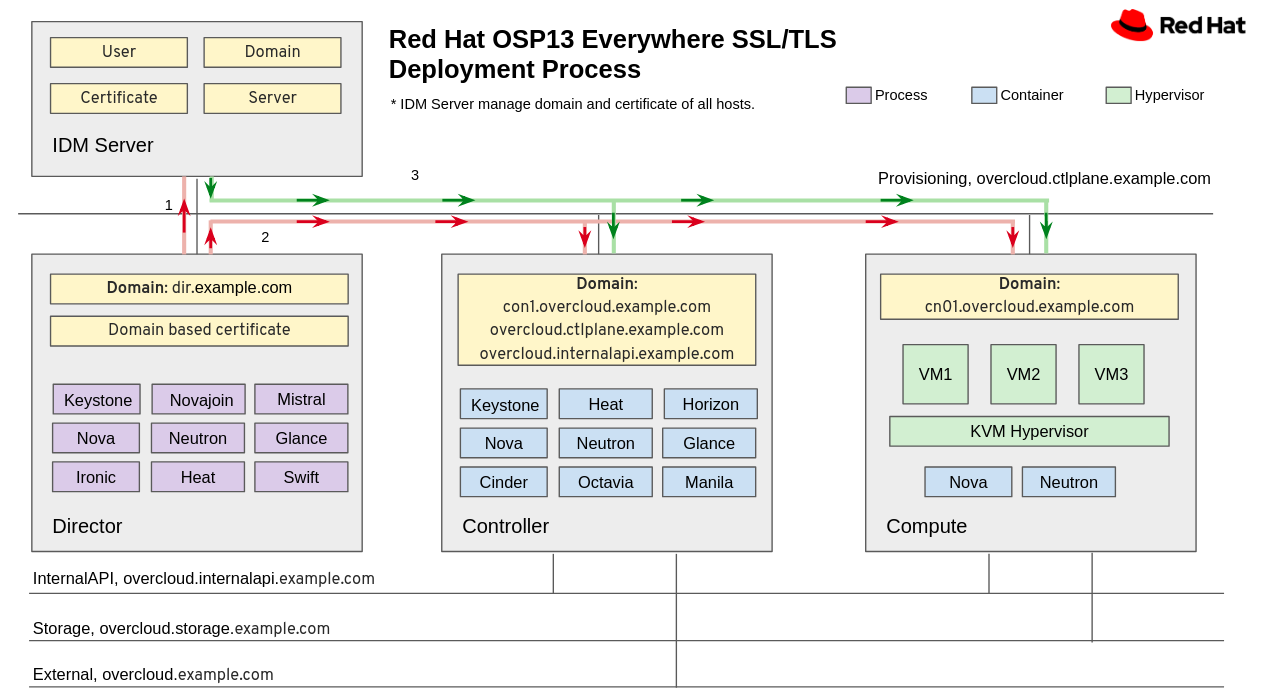
It has installed openstack packages in the director nodes. The packages are for installing openstack to other baremetal nodes. Let's see the process. 1. First, the director node registered domain to the IDM server. 2. And director will install controller and compute nodes with IDM server. 3. IDM server will check domain of overcloud's nodes and give the certificate to overcloud nodes.
If it finish to install openstack by director node, its system architecture is like below.
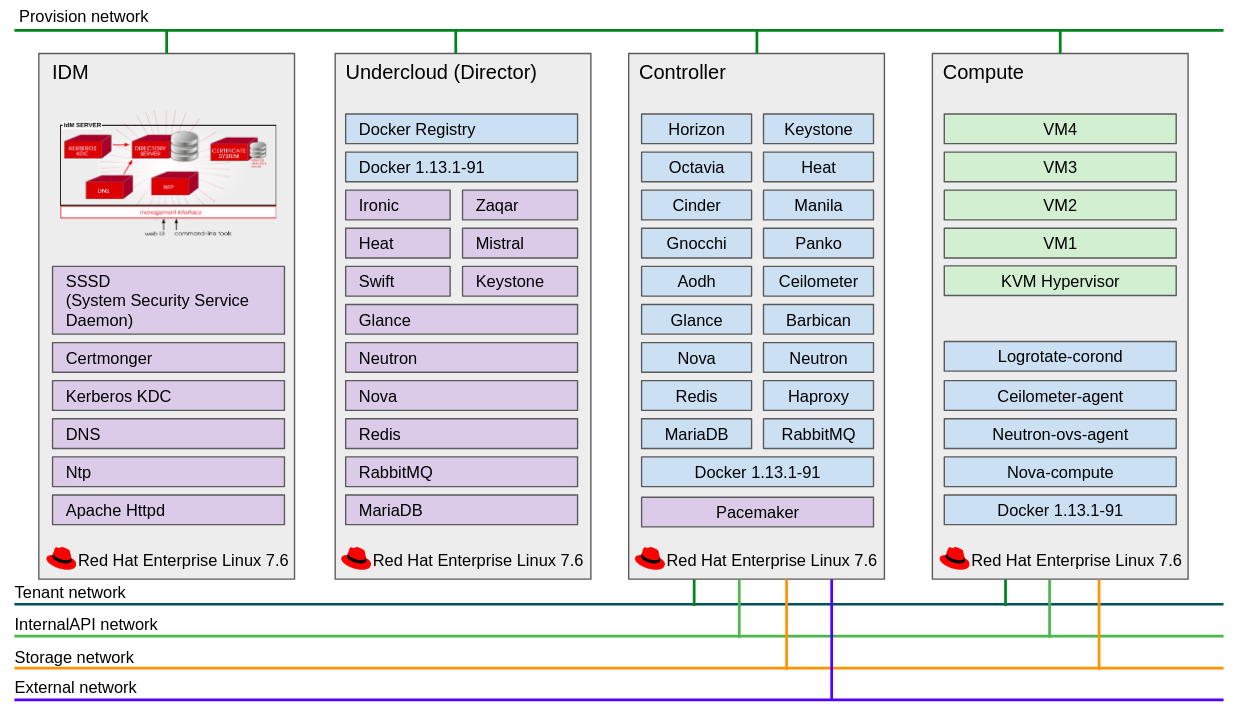
IDM server has apache httpd, ntp, dns, kerberos KDC, certmonger and SSSD(System Security Service Daemon)
Theses services provides features about manage overcloud nodes, domains, certificates and etc.
Director has openstack packages for overcloud(openstack for service) and docker. Because Openstack 13 version(queens) changed overcloud components. Previous openstack was installed only packages. Nowadays openstack main services are working in docker container.
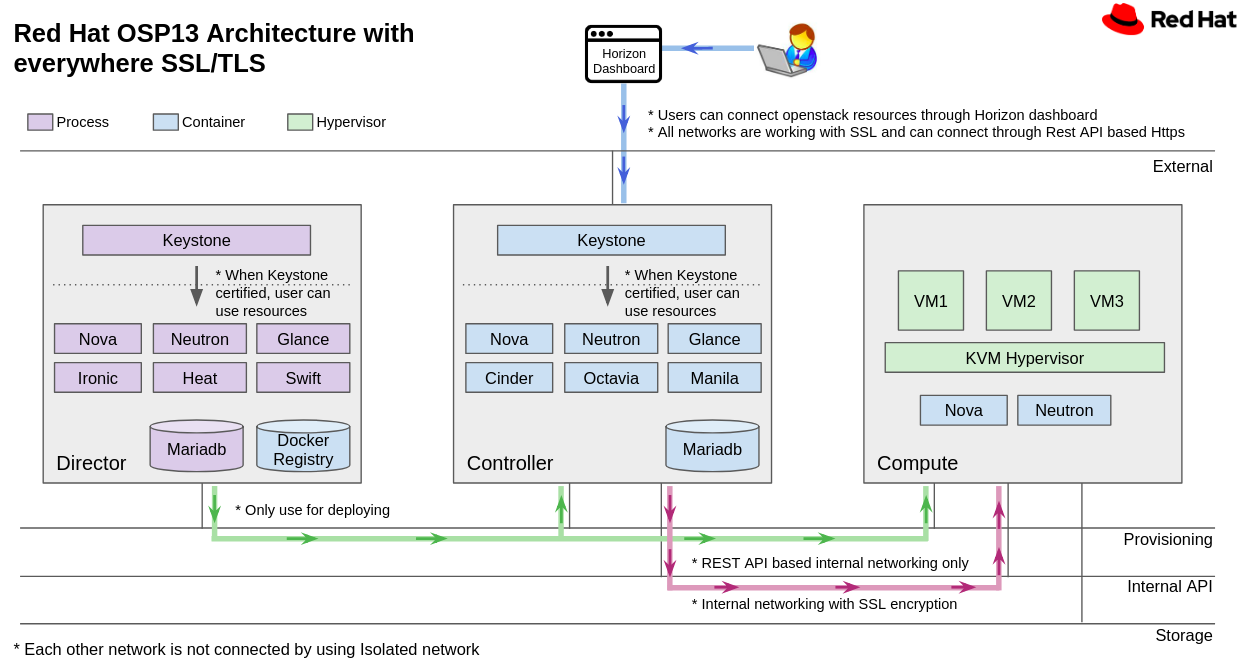
If it install OpenStack with everywhere SSL/TLS, users can access by https based external network only. And each services can communicate with SSL/TLS only. The resources of OpenStack must certify by Keystone. If the certification is succesful, users can use OpenStack services. Also all networks of OpenStack isolated by network purpose. so If we design like below network, this OpenStack services will be secure.
How is this posting? If you have any opinion, please let me know it.
If I have free time, I will post about docker containers of openstack.
'OpenStack' 카테고리의 다른 글
| Http 보안 및 용어 정리 (3) | 2019.09.30 |
|---|---|
| OpenStack Container (1) | 2019.06.07 |
| Octavia Amphora Instance (0) | 2019.05.10 |
| Load balancer as a service Octavia (0) | 2019.05.06 |
| openstack heat template for create network and server (3) | 2018.03.13 |
- Total
- Today
- Yesterday
- ubuntu
- 파이썬
- command
- 뉴트론
- NOVA
- Python
- 설치
- 쿠버네티스
- 오픈스택
- Network
- 김미경
- neutron
- 명령어
- 오픈쉬프트
- cpu
- Swift
- 후기
- sdn
- Java
- Redhat
- 레드햇
- 클라우드
- 네트워크
- 우분투
- install
- openstack
- 컨테이너
- OVN
- 세미나
- 하둡
| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | ||||||
| 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 | 21 | 22 |
| 23 | 24 | 25 | 26 | 27 | 28 | 29 |
| 30 | 31 |
